- Windows Xp Wanna Cry Patch Download Full
- Wannacry Xp Patch Download
- Windows Xp Wanna Cry Patch Download Free
- Windows Xp Wanna Cry Fix
Microsoft on Friday took the unprecedented step of issuing patches for long-demoted versions of Windows, including Windows XP, to immunize PCs from fast-spreading ransomware that has crippled machines worldwide.
So, if your organization, for some reason, is still running on Windows XP or Vista, you are strongly advised to download and APPLY PATCH NOW! WannaCrypt, or also known as WannaCry, is a new ransomware that wreaked havoc across the world last night, which spreads like a worm by leveraging a Windows SMB vulnerability (MS17-010) that has been. Microsoft issues first Windows XP patch in 3 years to stymie 'WannaCrypt'. Microsoft published patches for Windows XP, Windows 8 and Windows Server 2003. Or if users were required to.
To stymie 'WannaCrypt' attacks -- which encrypted files on thousands of PCs used by the U.K.'s National Health Service (NHS), causing chaos in many hospitals -- Microsoft published patches for Windows XP, Windows 8 and Windows Server 2003. All had been retired from support: Windows XP in April 2014, Windows 8 in June 2016, Windows Server in July 2015.
'We are taking the highly unusual step of providing a security update for all customers to protect Windows platforms that are in custom support only, including Windows XP, Windows 8, and Windows Server 2003,' said Phillip Misner, a principal security group manager at the Microsoft Security Response Center (MSRM), in a post to a company blog late Friday.
In fact, Microsoft has never issued security updates for software as long retired from support as Windows XP, which fell off the list more than three years ago.
Microsoft had the Windows XP, 8 and Server 2003 updates already in hand -- they were versions of MS17-010, a six-vulnerability fix delivered in March to newer editions, such as Windows 7 -- because it offers post-retirement assistance to corporate customers under a pay-for-patches program called 'Custom Support.'
The WannaCrypt ransomware spreads to other Windows PCs on a network by exploiting the vulnerabilities Microsoft patched with MS17-010; the malware can also infect other systems by sniffing for vulnerable machines connected to the public Internet. After WannCrypt is installed, it encrypts data on the PC, then displays an extortion note demanding between $300 and $600 to unlock the files.
Windows Xp Wanna Cry Patch Download Full
'Given the potential impact to customers and their businesses, we made the decision to make the Security Update for platforms in custom support,' Misner said in explaining Microsoft's motivation. 'This decision was made based on an assessment of this situation, with the principle of protecting our customer ecosystem overall, firmly in mind.'
The fact that news reports widely cited Windows XP-powered PCs as instrumental in the worm-like spread of WannaCrypt -- including in the NHS' networks -- was almost certainly a factor in Microsoft's decision. In early 2014, prior to Windows XP's retirement, the U.K. government contracted for one year of custom support. The Government Digital Service did not renew the contract, leaving XP machines helpless in the face of attacks after April 2015.
Significant numbers of users still run Windows XP and Windows 8, two of the out-of-date versions that Microsoft updated Friday. According to analytics vendor Net Applications, 7.7% of all Windows PCs run XP and 1.7% run Windows 8. Together those editions power more than 150 million PCs worldwide.
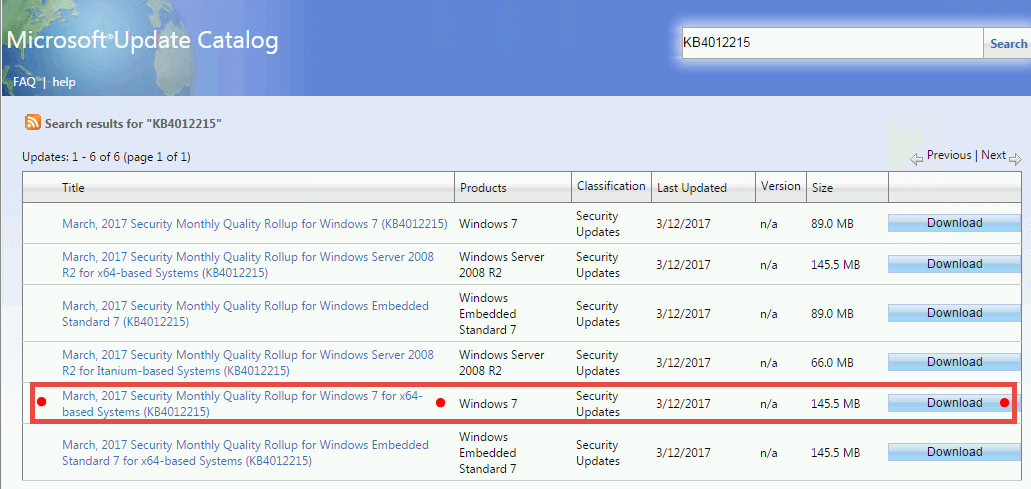
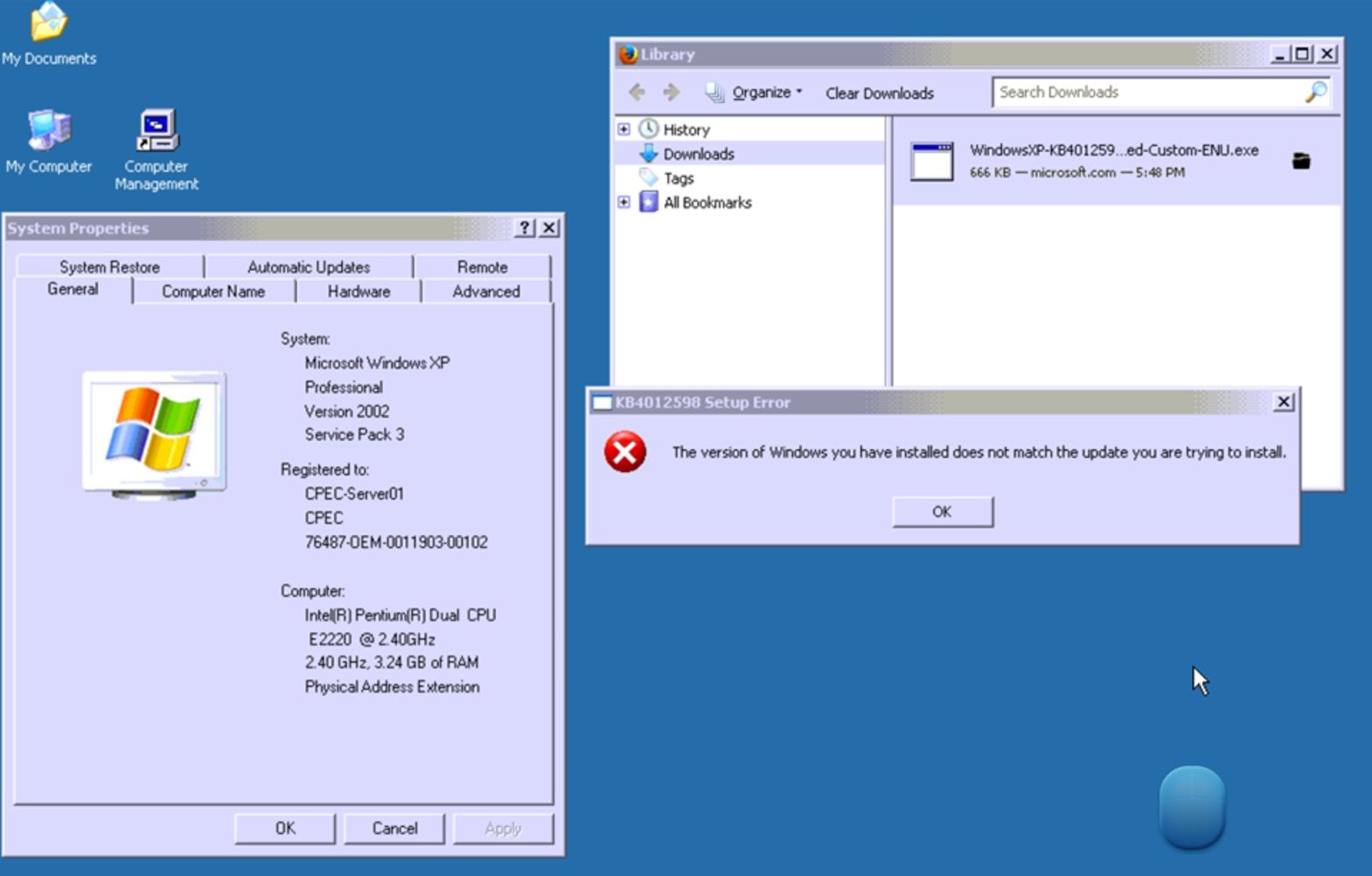
It was unclear Sunday whether Microsoft was delivering the new Windows XP, Windows 8 and Windows Server 2003 patches via the standard Windows Update maintenance service, or if users were required to manually download the appropriate fixes from the Update Catalog.
Following the massive Wana Decrypt0r ransomware outbreak from yesterday afternoon, Microsoft has released an out-of-bound patch for older operating systems to protect them against Wana Decrypt0r's self-spreading mechanism.
The operating systems are Windows XP, Windows 8, and Windows Server 2003. These are old operating systems that Microsoft stopped supporting years before and did not receive a fix for the SMBv1 exploit that the Wana Decrypt0r ransomware used yesterday as a self-spreading mechanism.
That mechanism is a modified version of the ETERNALBLUE exploit, an alleged NSA hacking tool leaked last month by a group known as The Shadow Brokers.
Original MS17-010 patch didn't include XP/Win8 fixes
Wannacry Xp Patch Download
Microsoft had released a fix for that exploit a month before, in March, in security bulletin MS17-010. That security bulletin only included fixes for Windows Vista, Windows 7, Windows 8.1, Windows 10, Windows Server 2008, Windows Server 2012, and Windows Server 2016.
As the SMBv1 is a protocol that comes built-in with all Windows versions, the computers which did not receive MS17-010 remained vulnerable to exploitation via Wana Decrypt0r's self-spreading package.
Windows Xp Wanna Cry Patch Download Free
'Given the potential impact to customers and their businesses, we made the decision to make the Security Update for platforms in custom support only, Windows XP, Windows 8, and Windows Server 2003, broadly available for download,' Microsoft said in a statement. 'This decision was made based on an assessment of this situation, with the principle of protecting our customer ecosystem overall, firmly in mind.'
Researchers believe that Wana Decrypt0r — also referenced online as WCry, WannaCry, WannaCrypt, and WanaCrypt0r — infected over 141,000 computers.
While unconfirmed, many believe older Windows XP and Windows Server versions were the bulk of the infections pool, as they had no way to protect themselves.
Patch systems and disable SMBv1 where possible
Besides installing these out-of-band updates — available for download from here — Microsoft also advises companies and users to disable the SMBv1 protocol, as it's an old and outdated protocol, already superseded by newer versions, such as SMBv2 and SMBv3.
The current Wana Decrypt0r outbreak has been stopped last night after a security researcher found a kill switch. This is only temporary, as the attackers could release a new version of this threat. This is why patching the SMBv1 exploit is a better solution.
For those affected, you can discuss this ransomware and receive support in the dedicated WanaCrypt0r & Wana Decrypt0r Help & Support Topic. Bleeping Computer also published a technical analysis of the Wana Decrypt0r ransomware.